Linus Tech Tips Hacked - Single PDF Almost Destroyed their YouTube Empire

Ansari
Category : Hacking
Time to read : 3 mins

The Incident
YouTube channel takeovers have become increasingly common and a recent hack targeted Linus Tech Tips and other Linus Media Group channels. The Hacker was able to livestream crypto scam videos, change channel names, and even delete videos. But the channels have now been restored after the breach was detected and addressed.
The hacker bypassed password and two-factor protections by targeting session tokens that keep users logged in to websites.
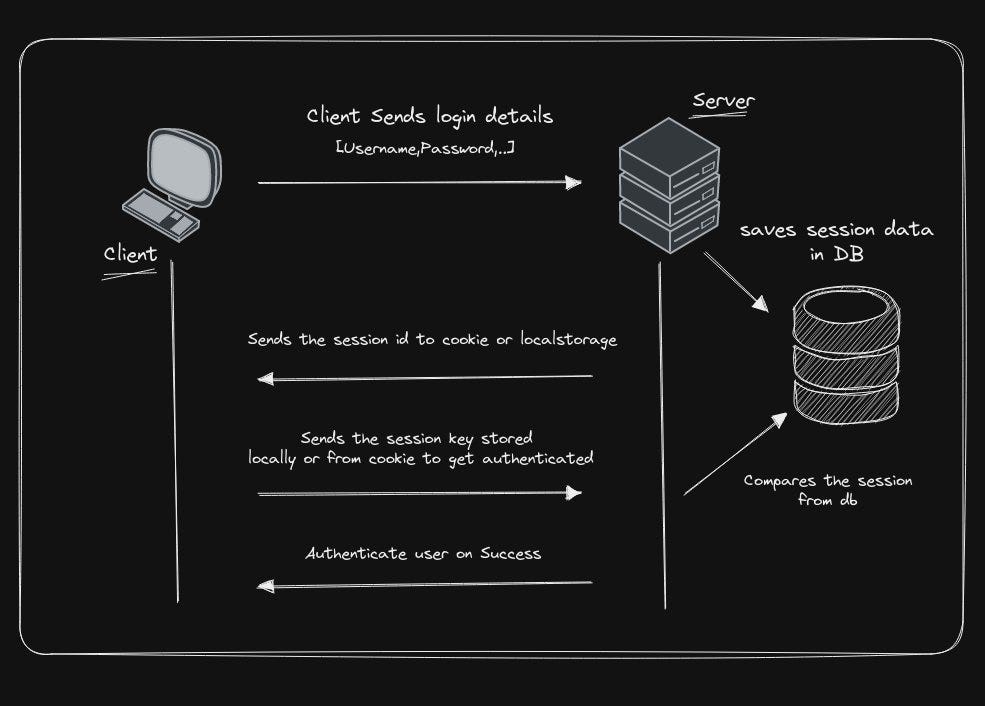
But what exactly is a session token? 🍪
A session token is a unique identifier that a website creates when a user logs in. It’s stored on the user’s device as a cookie or in local storage, and it’s sent with every subsequent request to the server.
Server uses the session token to identify the user and grant access to protected resources. For example if you log into your google in search page and then try to access your inbox, the session token tells the server that you’re authorized to view your messages.
Session token authentication flow 👇
Session tokens are often used in place of constantly asking for a username and password for each request. They also have an expiration time to ensure that users are logged out after a certain period of inactivity.
How these tokens were stolen ?
In the case of the Linus Tech Tips hack, the hacker was able to access session tokens and effectively gain access to the browsers of Linus Media Group’s team members. This allowed them to make changes and take over the channels without needing to enter any security credentials.
Linus explains that this is cause of a zip file they received from a source which looked like authenticated one. By downloading and extracting the zip, the .exe file hidden inside the PDF got executed and session tokens where extracted by the hacker.
To prevent these type of attacks ensure that any file you download from internet is from a legitimate source and Linus suggested that greater security options for certain channel attributes and confirmation or verification requests is needed to avoid such incidents.
It’s concerning that these types of hacks are becoming more common on Youtube. Hopefully, Sebastian’s recommendations and YouTube’s efforts will prevent future breaches and keep creators’ channels safe. Stay vigilant and protect your online accounts.
Thanks for reading the breakdown and how session tokens were used to bypass security measures. I hope this article has shed some light on the importance of properly securing online accounts and the potential risks of malicious downloads.
If you enjoyed this breakdown and want to stay up to date on the latest tech news and security threats, be sure to follow me for more interesting and informative content. I’ll continue to bring you the latest developments and insights on all things tech-related.